
Install SSL/TLS for Apache on Debian Video Guide
Pre-requisites:-
1: The server should have Apache installed.
How to Install Apache on your server:
a. Update your server -
shell
sudo apt update
b: Install Apache -
shell
sudo apt install apache2
c: Check the Installation of Apache WebServer
Either, run the command -
shell
systemctl status apache2
If you get an ACTIVE in your output, you're good to go.
OR
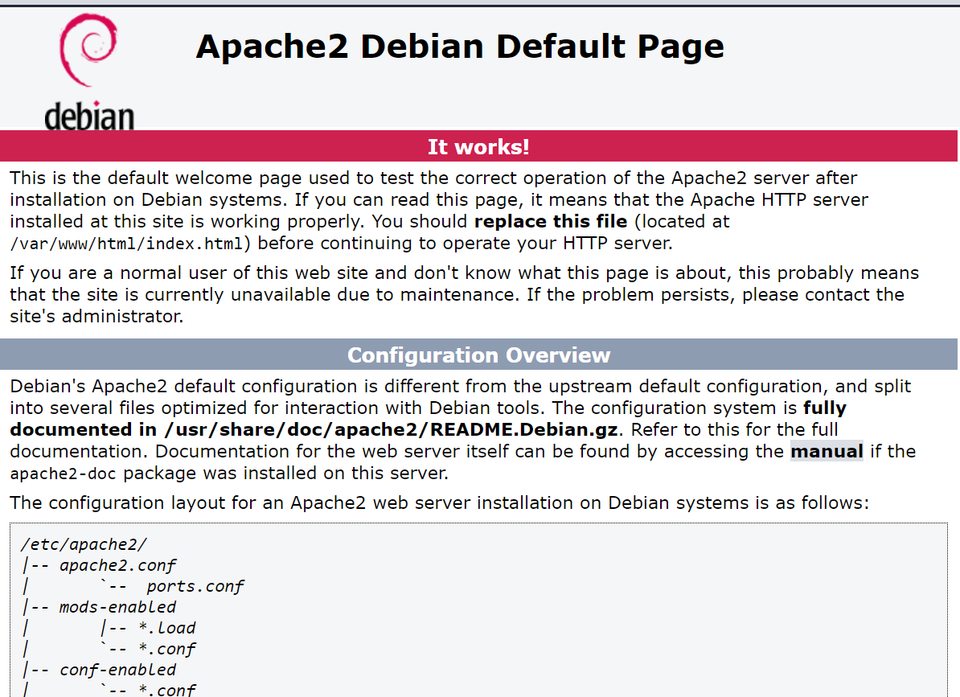
Head over to yourdomain.com and check whether you're able top see the default Apache Page which should look like this -
Step 1. Generating a CSR and Private Key with OpenSSL
You will first have to generate a private key and a CSR (Certificate Signing Request) using the default OpenSSL Library provided by Apache.
We are first going to make a directory to store of all our certificate files, including our private key and CSR.
1: To make a directory, type in the following command:
shell
sudo mkdir /etc/encryption
This will create a sub-directory under /etc called encryption. You can replace encryption with the name of your choice.
2: Type in the following command to generate a private key and a CSR -
shell
sudo openssl req -new -newkey rsa:2048 -nodes -keyout /etc/encryption/server.key -out /etc/encryption/server.csr
This will create a private key and a CSR with the name of server.key and server.csr respectively; in the encryption directory.
You will then get a prompt asking you to input the following details regarding your CSR:-
Country Name (2 letter code) [AU]: Type in the 2 letter abbreviation for your country.
State or Province Name (full name) [Some-State]: Full name of the state
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Locality Name (eg, city) []: Complete name of the city, no abbreviations
Organization Name (eg, company) [Internet Widgits Pty Ltd]: If you are a business; Enter your legal entity name. If you're not a business, any value entered will not be used in your certificate.
Organizational Unit Name (eg, section) []: If you are a business; Write the appropriate division of your company. It is best to use something generic such as "IT".
Common Name (e.g. server FQDN or YOUR name) []: Enter your domain name<
Email Address []: Enter your email address
After you hit Enter, your Private Key and CSR should be generated successfully in the directory named encryption.
3: To view your CSR, type in the following command:
shell
cat /etc/encryption/server.csr
You can now copy your CSR with CTRL+C and move on to configuring your SSL Certificate.
Step 2. Order and Configure the SSL Certificate
Now, we need to buy an SSL Certificate. If you visit our SSL Certificates List page, you will see options available, such as a low-cost domain-validated SSL or a wildcard SSL, which also secures the sub-domains.
Cheap SSL Certificates
View our low cost SSL Certificates with domain validation.
Starting at $ per year
If you require any assistance with selecting an SSL Certificate, please feel free to contact our sales team and they will be happy to assist.
2: Once you have completed the SSL Certificate Purchase you can begin the configuration process. This can be started by going into your SSLTrust account and managing your recent purchase.
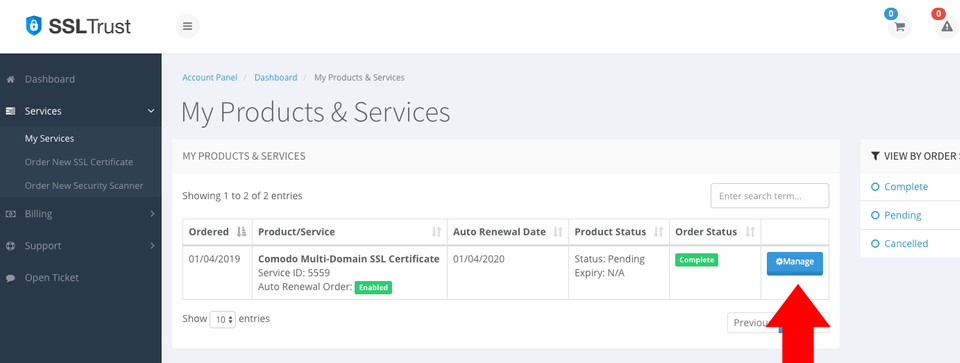
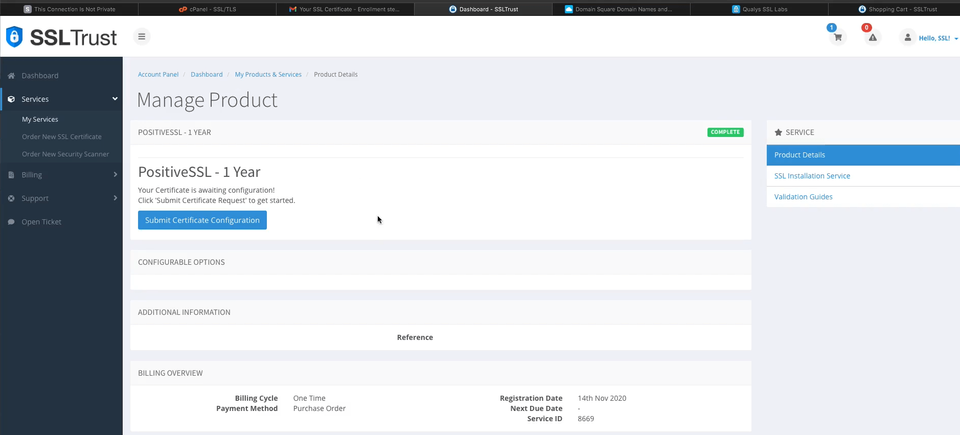
You then will need to click the Submit Configuration button to begin the configuration process.
3: You now need to paste in the CSR you generated using the OpenSSL library in the Debian CLI. This includes the lines:
text
-----BEGIN CERTIFICATE REQUEST---- -----END CERTIFICATE REQUEST-----
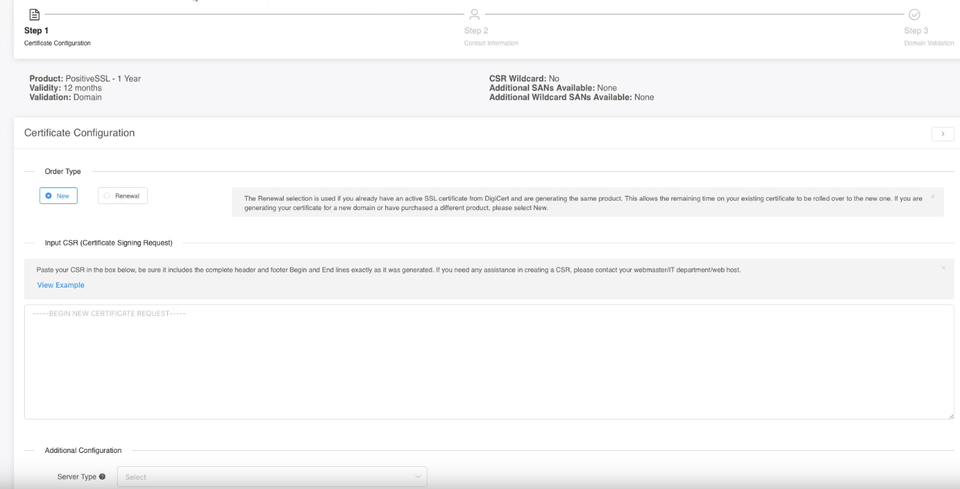
Select Apache for your Web Server Type.
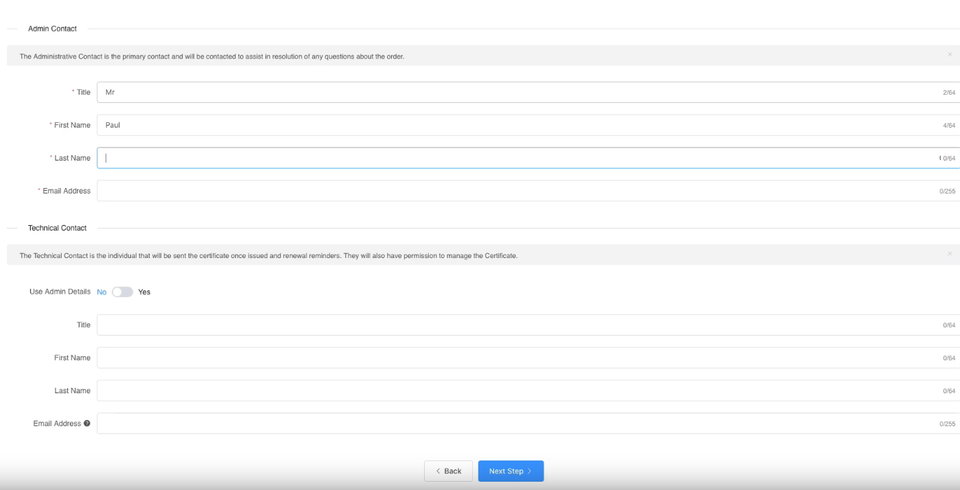
You will need to also enter the Site Administrator Contact Information.
This information is to be of the individual who is responsible to approve and SSL Certificate. If it is a business SSL, it needs to be a contact under the business.
The Technical Contact Information is the details of the individual responsible for the installation and management of the Certificate.
If you have ordered a business SSL, you will also be required to enter your business details. These should be the correct address and phone number and legal entity name. They will be required to be validated by the Certificate Authority, any mistakes will cause delays. More information on Business Validation can be found here.
4: Click Continue to go to the next Step. Here you need to select the Authentication Method to validate your domain name. This is required to prove you own the domain name and have permission to issue an SSL Certificate for the domain.
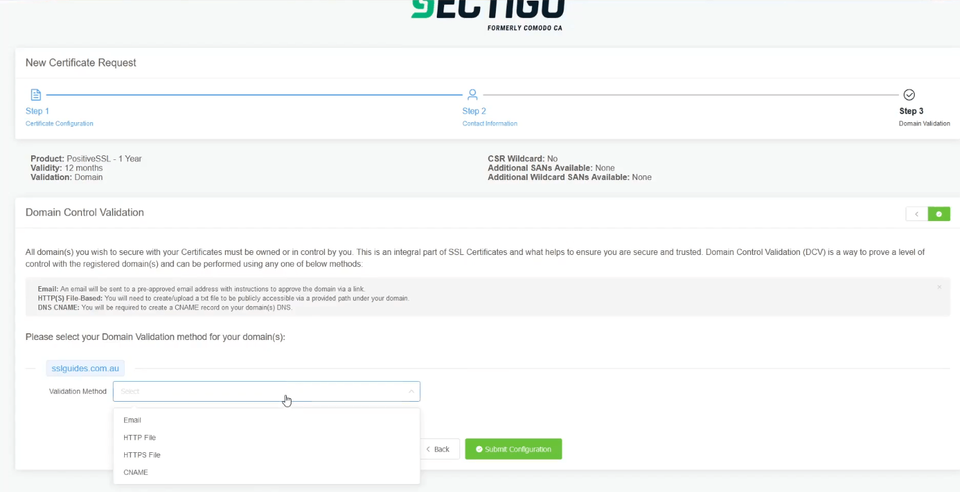
Select the method that will be the easiest for you to use; File-Based Authentication ( HTTP / HTTPS ), CNAME Based Authentication ( DNS ) or Certificate Approver Email.
If you have access to one of the listed emails, this can be the quickest method
Click Continue/Submit to finish the Configuration process.
After you complete the domain validation via your selected method, your SSL will be issued. If you ordered a Business SSL, you will need to wait for the Certificate Authority to complete the Business address and phone validation. If the validation has not progressed, or you have not received your Certificate after some time, please contact our support team so we can check on its status.
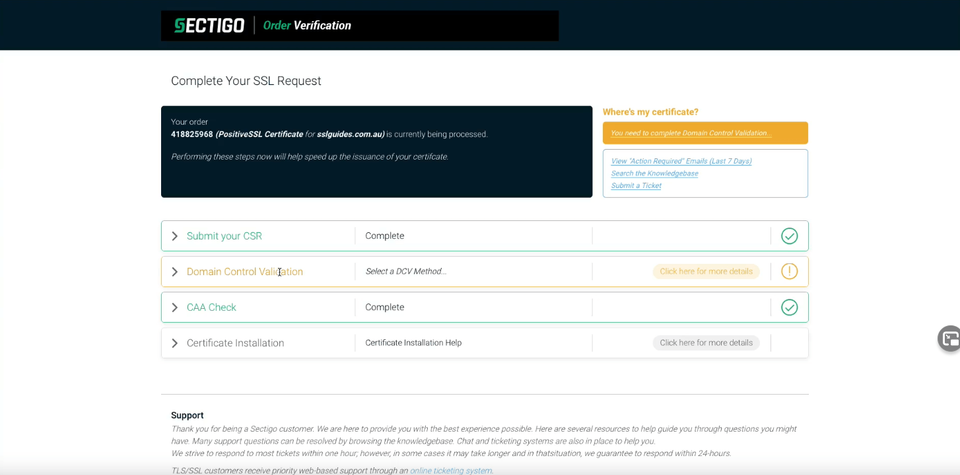
Step 3. Upload the SSL Certificate files to your server
When your SSL Certificate has been issued, you will be emailed the Certificate Directly from the Certificate Authority. You can also download it from your SSLTrust Portal. Downloading it from the SSLTrust Portal is a good option as we format the certificate in an easy to use way.
Again; View your certificate management page within SSLTrust
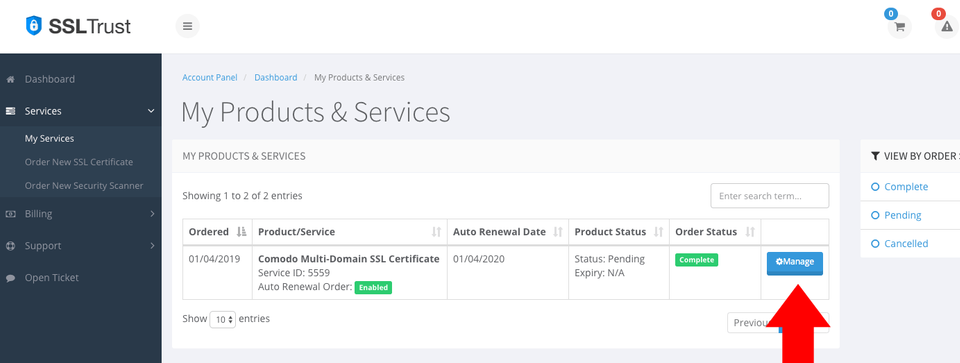
1: Click on the Manage button and collect/download your certificate
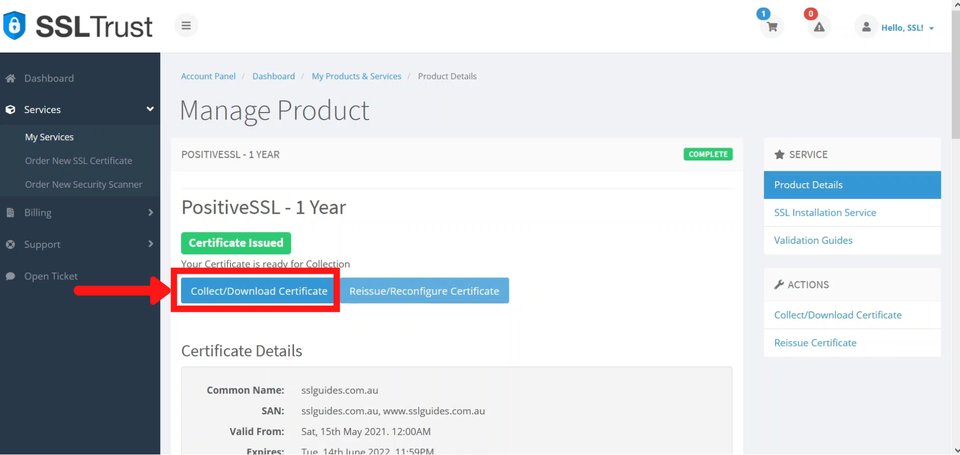
2: Go to the first column and click on copy to clipboard
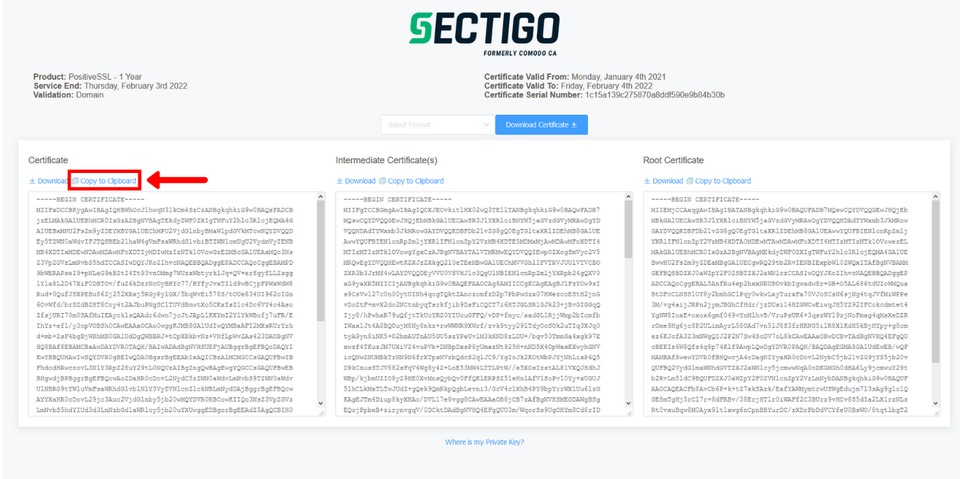
3: Open your SSH Client and type in the following command
shell
sudo nano /etc/encryption/certificate.crt
Paste in your certificate while saving the buffer and click on exit (CTRL+X).
The above command enabled you to save your certificate to the encryption directory.
4: Head over to the certificate collection page and click on copy to clipboard on the Intermediate certificate.
Note:- It is recommended that you install your intermediate certificate too so as improve compatibility with browsers; and to minimize the chances of your visitors getting unwanted security warnings on your website.
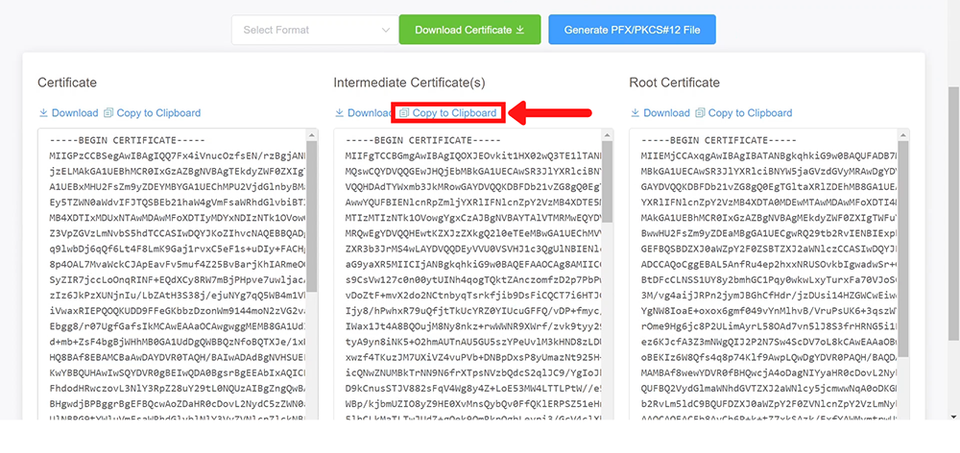
5: Type in the following command and paste your intermediate certificate.
shell
sudo nano /etc/encryption/intermediate.crt
Save the buffer and exit by pressing CTRL+X
After having uploaded the certificate files to your server, it is now time to configure Apache SSL Parameters
Step 4. Configure the Apache SSL Parameters
1: Let's create an SSL Parameters file and edit it
shell
sudo nano /etc/apache2/conf-available/ssl-params.conf
2: Copy and paste the following set of directives:
text
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1 SSLHonorCipherOrder On # Disable preloading HSTS for now. You can use the commented out header line that includes # the "preload" directive if you understand the implications. # Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload" Header always set X-Frame-Options DENY Header always set X-Content-Type-Options nosniff # Requires Apache >= 2.4 SSLCompression off SSLUseStapling on SSLStaplingCache "shmcb:logs/stapling-cache(150000)" # Requires Apache >= 2.4.11 SSLSessionTickets Off
Save and exit the buffer.
Step 5. Configure the Apache Virtual Host
1: Create a backup of the respective default virtualhost configuration; This will make sure that Apache can revert to the older configuration incase of any syntax errors.
shell
sudo cp /etc/apache2/sites-available/default-ssl.conf /etc/apache2/sites-available/default-ssl.conf.bak
2: Proceed to the edit the default Apache Virtual Host Configuration
shell
sudo nano /etc/apache2/sites-available/default-ssl.conf
Provide the proper directory and configuration name incase your have multiple virtual hosts on your server. This is for the default Virtual Host.3: Make sure the configuration matches with the format below. Replace yourdomain.com with your domain name and make sure to provide the correct paths for both the certificates and the private key.
text
<IfModule mod_ssl.c>
<VirtualHost _default_:443>
ServerAdmin youremail.com
DocumentRoot /var/www/html
ServerName yourdomain.com
ServerAlias www.yourdomain.com
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SSLEngine on
SSLCertificateFile path-to-certificate.crt
SSLCertificateKeyFile path-to-private-key.key
SSLCertificateChainFile path-to-intermediate-cert.crt
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
</VirtualHost>
</IfModule>
Optional: Redirect HTTP to HTTPS
shell
sudo nano /etc/apache2/sites-available/000-default.conf
replace the path if you have multiple virtual hosts set up.
text
<VirtualHost *:80> ServerAdmin youremail.com DocumentRoot /var/www/html ServerName yourdomain.com ServerAlias www.yourdomain.com Redirect "/" "https://your_domain_or_IP/" </VirtualHost>
Step 6. Update the Firewall Settings
1: Check the applications enabled by the Firewall
shell
sudo ufw app list
2: It is recommended that you have your firewall enabled and make sure to allow port 443 or type in the following command:
shell
sudo ufw allow 443 sudo ufw allow 80
This will allow both HTTP and HTTPS ports to allow incoming traffic. 443-HTTPS and 80-HTTP.
Step 7. Step 7: Enable the mod_ssl module and other configurations
Enable the Apache mod_ssl and mod_headers module
shell
sudo a2 enmod ssl sudo a2 enmod headers
Enable the default SSL Configuration
shell
sudo a2ensite default-ssl
Enable the default SSL Parameters file
shell
sudo a2enconf ssl-params
Test the Apache Configuration. If you get the message "Syntax Ok" , then we're good to go. Do not worry about the ServerName Global Directive Error.
shell
sudo apache2ctl configtest
Restart the Apache WebServer and proceed to check your installation.
shell
sudo systemctl restart apache2
Step 8. Check the SSL is working
SSLTrust's Free SSL Checker is a tool that allows you to test and validate the SSL/TLS certificates installed on websites. Simply enter a domain name and it will analyze the certificate, providing details like the issuer, expiration date, encryption strength, and whether the certificate is properly configured and trusted by major browsers and operating systems. In SSL tests, receiving an "A" rating typically signifies that the SSL certificate and its configuration meet high security standards.
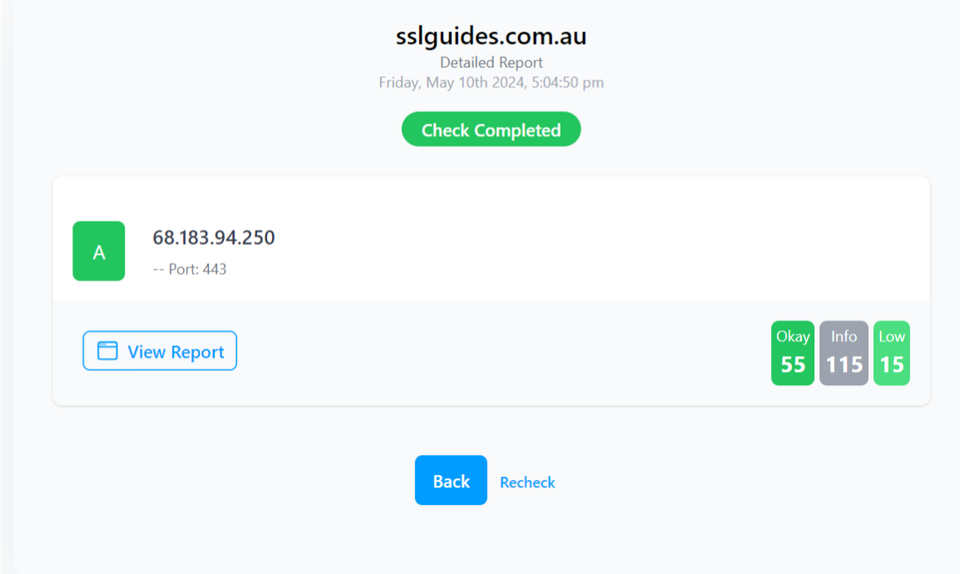
The checker highlights any potential security issues or misconfigurations with the SSL implementation. This free tool makes it easy to verify if a website's SSL certificate is valid and secure, giving visitors confidence their connection is encrypted and their data is protected from eavesdroppers.
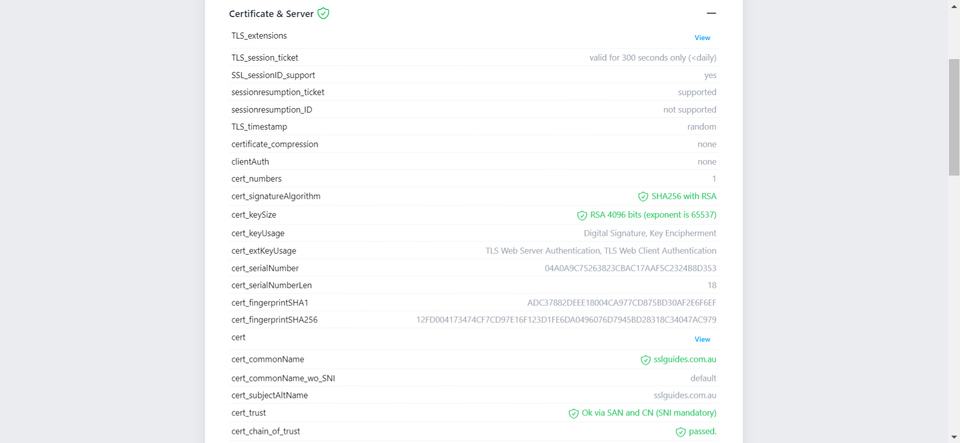
Additionally, you can also performed a detailed check which generates an actionable report with all the ins and out of your SSL Certificate. This includes Protocols, Ciphers, Vulnerabilities and much more.
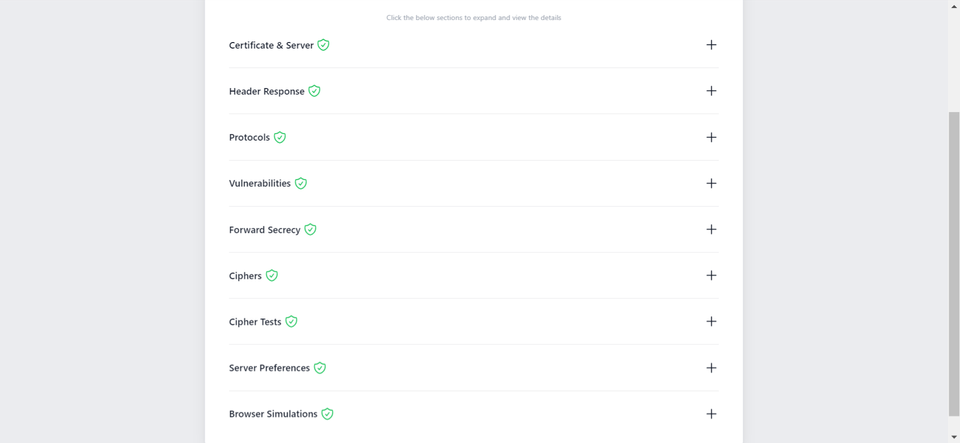
-
You might require assistance from your web developer or make the necessary updates to your website personally to ensure that all files utilize "https://" and all links leading to and within your website employ "https://".
Discussions and Comments
Click here to view and join in on any discussions and comments on this article.





